You will not need passwords any more
A new paradigm of passwordless login is going to come to all services very soon. Expect to abandon all your passwords by the end of this year.
There has been a need to protect secrets since time immemorial. A cipher is an algorithm or a rule, based on which a message can be encrypted. The simplest cipher is called the replacement cipher where one letter is replaced by another such:
A is replaced by W
B is replaced by K and so on…
The problem with such a cipher is that you need to get the key across to the reader before they can decipher it. This creates what is called the Key Distribution problem. You cannot send the message and the key together because if the message is intercepted then it will also be decrypted. Or you need to send two messengers across for each message.
Alternately you can have rule-based ciphers such as
A = A+3 or D and so on for every letter.
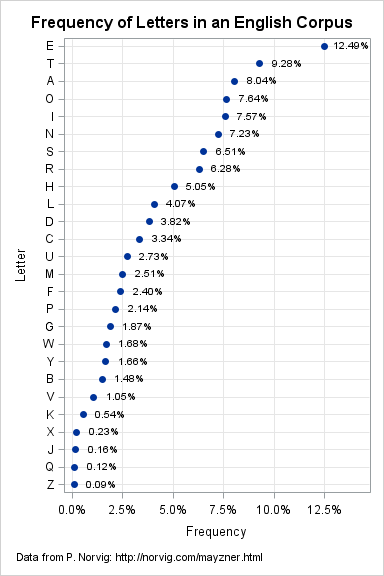
The trouble with all rule-based cipher is that they can be easily broken using statistical analysis. In English, E is the most used alphabet followed by T and A. You could perform statistical analysis on any message and figure it out.
Source: SAS
Every language suffers from this problem.
The Germans came up with the Enigma Machine that changed the Cipher after every letter. So simple statistical analysis would not work. Only another enigma machine with the right key could decipher it and that key was changed every day. It could be broken by statistical analysis, only you needed millions of calculations to be done in less than a day and some human stupidity. In order to crack the Enigma, Alan Turning invented the modern computer.
His contribution to the allied victory in the second world war cannot be understated. He struggled to get his work funded, he struggled to make dim-witted officers see the relevance of his work and then he was harassed into suicide by the British government for being gay. Such nice people these British are.
Then with the advent of the computer age came three researchers; Ron Rivest, Adi Shamir and Leonard Adelman, who in 1977 gave us the Rivest - Shamir - Adelman or RSA Cryptosystem. The simple idea was to create what is like a padlock which can be click locked but needs a key to open it. So anybody can buy the lock and lock a box/message but only those with the key can unlock it. The equivalent of the lock is the public key and the key is the private key which only you possess.
While I do not want to dive into the complex mathematics of it, the simple explanation is -
If you were to take two prime numbers and compute the remainder, say 2, you can guess that the primes are 7 and 5 or 11 and 13 or so on. What number I had used is private to me. In mathematics, the remainder is calculated using a step function or modulus function. The modulus function is called an irreversible function.
But if I were to take longer primes. In the case of 256-bit encryption, a 256 digit prime number is used. It is even harder for you to work your way back from it. Even so, it would take a matter of hours if you were to unleash the might of online servers today. We are currently up to using 1024 bit encryption.
If you really want to know how this works, you can read the link above. If you want to read it as a story, read the Code Book by Simon Singh.
This mathematics is reduced to a private key and a public key. You can encrypt using the public key but decrypt using only a private key.
Password
Now, every one of us uses passwords to log in to accounts and the people creating the platform have a strange conundrum to deal with. You can allow a user to have a single character password but it would be super easy to hack it. Or you could have the user create a password which has:
One uppercase letter
One lowercase letter
One number
One symbol
and is 15 characters long
And then you forget what you had used. As with the encryption above, the longer the password, the harder it is to crack it.
Force the user to create very complex passwords and they will end up locking themselves out. Give them super easy passwords and they will end up hacked. Also, most of us use numbers that have significance in our lives, so get hold of someone’s birthday, anniversary, etc and it becomes possible to socially engineer the password with a few guesses.
And then came two-factor authentication. Use a password and a one-time system-generated password sent either through a message or an authenticator app. This has increased safety many folds because it might be possible to guess your password, but who is going to guess your random number?
Almost every smartphone in the world now uses a biometric ID. Either a fingerprint scanner or face recognition software is standard in most high-end smartphones. Also, most people have one and have it on them almost all of the time.
Enter FIDO
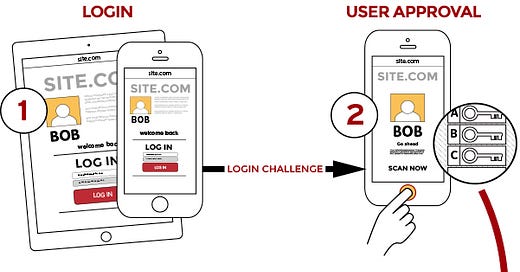
Given that two-factor seems to work so well, why do we need the password at all? Let us create a system based handshake that is being authenticated by the user's biometrics
FIDO Alliance is a standards organisation that is engaged in building authentication standards and given the above facts, they are proposing…
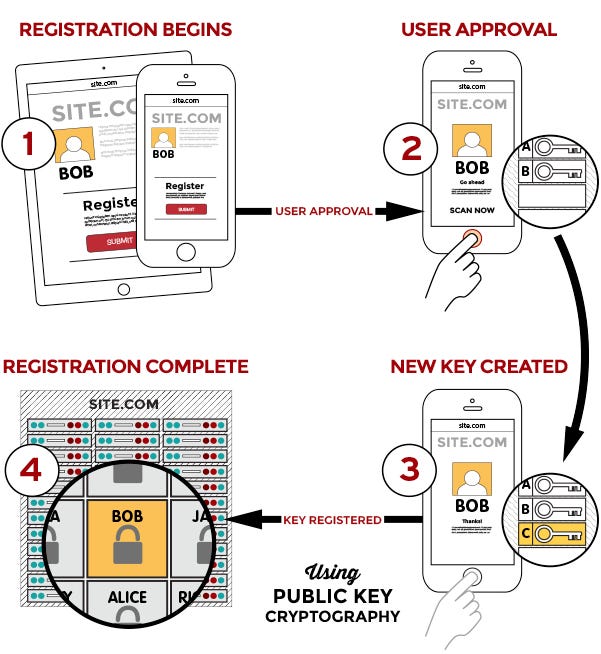
The FIDO protocols use standard public key cryptography techniques to provide stronger authentication. During registration with an online service, the user’s client device creates a new key pair. It retains the private key and registers the public key with the online service. Authentication is done by the client device proving possession of the private key to the service by signing a challenge. The client’s private keys can be used only after they are unlocked locally on the device by the user. The local unlock is accomplished by a user–friendly and secure action such as swiping a finger, entering a PIN, speaking into a microphone, inserting a second–factor device or pressing a button.
Source: FIDO
In practice
Source: FIDO
In a joint effort to make the web more secure and usable for all, Apple, Google, and Microsoft today announced plans to expand support for a common passwordless sign-in standard created by the FIDO Alliance and the World Wide Web Consortium. The new capability will allow websites and apps to offer consistent, secure, and easy passwordless sign-ins to consumers across devices and platforms.
[…]
Hundreds of technology companies and service providers from around the world worked within the FIDO Alliance and W3C to create the passwordless sign-in standards that are already supported in billions of devices and all modern web browsers. Apple, Google, and Microsoft have led development of this expanded set of capabilities and are now building support into their respective platforms.
These companies’ platforms already support FIDO Alliance standards to enable passwordless sign-in on billions of industry-leading devices, but previous implementations require users to sign in to each website or app with each device before they can use passwordless functionality. Today’s announcement extends these platform implementations to give users two new capabilities for more seamless and secure passwordless sign-ins:
Allow users to automatically access their FIDO sign-in credentials (referred to by some as a “passkey”) on many of their devices, even new ones, without having to reenroll every account.
Enable users to use FIDO authentication on their mobile device to sign in to an app or website on a nearby device, regardless of the OS platform or browser they are running.
In addition to facilitating a better user experience, the broad support of this standards-based approach will enable service providers to offer FIDO credentials without needing passwords as an alternative sign-in or account recovery method.
Source: Apple
So get ready to ditch your passwords completely and move to the device based authentication paradigm. For many consumers, this is going to prove to be a godsend.
It is hard to remember different passwords for different sites. Most of us use 1 or 2 passwords and 5 or 6 variants of it over and over on every site. If a hacker finds one, almost all other sites are equally exposed.
After this, your passwords are going to look like this -
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDj8B02hBJmjs0h0grqA1VBZ5Mn2YACRDWalYsQgYt4qmUt2lEQfRyg2RAHFkCgbHM25nAo27xJtLmUbDswO5FtSVHkJV6Nkf1WIwHjqtd8HDKoVzQALwqwZfHzc5K2XsdFYkeY21/T0Ls92b0j9MyKMh/qIl29JU9JXVQUjuU9LsdNCOLoA+9+YLnwGh6Wg5N0kyrI1mvuQKtazHUGtAeVDg/8sNdRsFWG89Kp+T8kAYu72UjDRK3PKR1oYCgGm2bMFlF9R6ODshmP9d1lTJm7gwW8O/DyYh/V6GPY
-----END PRIVATE KEY-----
And even you will have never seen it!




Very Informative Read, Look into implementing POC with this standard and share my experience here