Internet | Learning by Proxy
Internet runs on software that most of us don't even know exists. It is run by those who don't get paid to maintain that software. One day they may decide not to.
All of us use the internet. The mere fact that you are reading these words is because of the internet. Today, your phone has software, your car has software, your refrigerator has software, even my weighing scale has a software. Software is everywhere. Have you ever wondered what software the internet runs on?
The internet was originally created as a project to communicate with soldiers on the battlefield. As the war with Russia (the hot one, not the cold one) never came to pass, that same technology found other applications. People started experimenting and building on it. The fundamental was to build a system through which data could flow. A protocol. While there were many competing protocols, the one that was free eventually won out. It is called the HyperText Transfer Protocol (HTTP).
HTTP is like the pipes that regulate the flow of data on the internet. That data needs to be stored somewhere. Servers store those data. Webservers are software that helps a server handle HTTP requests.
Open-source software (OSS) is computer software that is released under a license in which the copyright holder grants users the rights to use, study, change, and distribute the software and its source code to anyone and for any purpose. Open-source software may be developed in a collaborative public manner. Open-source software is a prominent example of open collaboration, meaning any capable user is able to participate online in development, making the number of possible contributors indefinite. The ability to examine the code facilitates public trust in the software.
Source: Wikipedia
Open-source software allows anyone to alter the source code and create a newer, better version, or add features and share it. Often many people simultaneously work on open source software and share their development with the rest of the developer community working on it. This makes the software better for everyone. Keeping it open source also makes it free to use.
While there were several competing server technologies including the likes of Microsoft and Oracle; most of the tinkerers who went on to build almost everything you use on the internet used Open Source Software for their servers because it is free. I can get a WordPress server with software setup for $5 today. That is the startup cost on the internet.
The Apache HTTP Server was one of the most popular open-source server software released in 1995. It is Open source (explained above), cross-platform (works on various hardware), web-server software. WordPress powers about 30% of all websites on the internet, it runs on Apache.
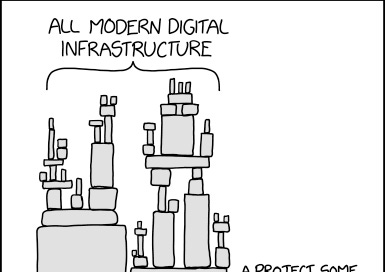
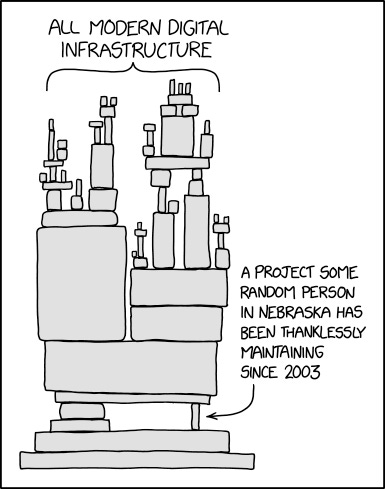
In the spirit of Open Source Software, a developer by the name of Ceki Gülcü created a Java-based logging utility called Apache Log4j. Log files store what is happening within certain systems so that if an error occurs it is possible to figure out what went wrong.
When a utility is useful many people adopt it. It comes down to the person who wrote it, to maintain it. Often there are several bugs that get discovered over time and they need to be fixed as they get discovered.
Source: XKCD
Log4J was written in 2001 and that developer has been maintaining it since - free of cost. But, last week a zero-day vulnerability was discovered which allows arbitrary code execution.
A zero-day (also known as 0-day) is a computer-software vulnerability either unknown to those who should be interested in its mitigation (including the vendor of the target software) or known and a patch has not been developed. Until the vulnerability is mitigated, hackers can exploit it to adversely affect programs, data, additional computers or a network.
Source: Wikipedia
Think of it as a birth defect that you just realised exists.
Arbitrary code execution allows the attacker to run any code that they wish on the machine.
Last week it was discovered…
The vulnerability in Log4J is extremely easy to exploit. After sending a malicious string of characters to a vulnerable machine, hackers can execute any code they want. Some of the earliest attacks were kids pasting the malicious code in Minecraft servers. Hackers, including some linked to China and Iran, are now seeking to exploit the vulnerability in any machine they can find that’s running the flawed code.
And there’s no clear end in sight. The Log4J issue amounts to a long-term security crisis expected to last months or years. Jen Easterly, director of the US Cybersecurity and Infrastructure Security Agency, has said this is “one of the most serious flaws” she’s ever seen.
Source: MIT Technology Review
The problem is that almost half the Internet is built using this and that means almost everything that we use is right now vulnerable at some level. The first problem is that there is no clear idea of the fix and they are working on it and besides who funds it?
“The team is working around the clock,” Yazici told me by email when I first reached out to him. “And my 6 a.m. to 4 a.m. (no, there is no typo in time) shift has just ended.”
In the middle of his long days, Yazici took time to point a finger at critics, tweeting that “Log4j maintainers have been working sleeplessly on mitigation measures; fixes, docs, CVE, replies to inquiries, etc. Yet nothing is stopping people to bash us, for work we aren’t paid for, for a feature we all dislike yet needed to keep due to backward compatibility concerns.”
[…]
As pressure and critics pile on the Log4J team, old questions of fairness are being asked about the open-source world.
“Fairness is a problem,” says Ceki Gülcü, who founded Log4 . “There’s this weird imbalance, where you profit from something but you don’t give anything back.”
The public is also almost completely ignorant of the immense role—and risk—of the free-labor-powered open-source software that runs the internet. OpenSSL powers encryption, for example, and Linux is behind the most widely used operating systems on the planet, including Android.
[…]
In 2018, the developer behind a popular open-source project called ua-parser-js quit, unwilling to work for free anymore. The software is used by big tech firms including Google, Amazon, and Facebook. The person who took control of ua-parser-js then hijacked the software and added malicious code to the project to steal cryptocurrency.
Source: MIT Technology Review
The greatest problem is that a lot of the infrastructure that we take for granted is built out of passion and love for software. Entrepreneurs who profess ‘passion’ don’t really build much of use. Even if they do, they use an elitist tool called Patents to put a lock on it. This stops it from being of any benefit beyond the same company. At the same time, they all continue to use all of the open-source solutions and build their wealth on them.
Wait there is more…
So far, the vanguard of Log4j hacking has primarily comprised cryptominers, malware that leeches resources off of an affected system to mine cryptocurrency. (These were extremely popular a few years ago, before everyone realized that the real money’s in ransomware.) Some nation-state spies have dabbled as well, according to recent reports from Microsoft and others. What’s seemingly missing is the extortion, the ransomware, the disruptive attacks that have defined so much of the past two years or so. This won’t be the case for long.
[…]
Log4Shell is also relatively trivial to exploit. Just send a malicious piece of code and wait for it to get logged. Once that happens, congratulations; you can now remotely run whatever code you want on the affected server.
It’s that combination of severity, simplicity, and pervasiveness that has the security community rattled. “It is by far the single biggest, most critical vulnerability ever,” says Amit Yoran, CEO of cybersecurity firm Tenable and founding director of US-CERT, the organization responsible for coordinating public-private response to digital threats.
So far, though, that calamity seems slow to manifest. Hackers are absolutely targeting Log4j; security firm Check Point has seen over 1.8 million attempts to exploit the vulnerability since Friday, according to spokesperson Ekram Ahmed. At some points, they’ve seen over 100 attempts per minute. And state-sponsored groups from China and Iran have been spotted using Log4Shell to establish footholds in various targets. Still, for now, cryptominers reign.
Source: WIRED
The foundation of what the internet stands on is being taken care of by soldiers who are often unpaid. Now, just imagine, not having the internet for 1 month or losing everything that you have stored on the internet. What would you pay to avoid that? Those who have profited off the internet should certainly start paying.



Let's go back to the good old analog